Why are we here again, looking at the deployment of Windows 11 to your Microsoft Intune managed devices?
Well, there’s still not long to go until Windows 10 gets killed off and you’re going to have to move to Windows 11, and four five six nine things:
- We should probably be using Entra App Registrations for authentication.
- Alberto Baratta on LinkedIn kindly pointed out that there was a way to improve the collection of the Readiness Report data.
- I’ve improved the processing of the Readiness report data after learning about hashtables.
- I encountered a situation where existing Windows Update for Business rings were deployed to groups of users 😅.
- If I’m saying you should be re-running the script on a regular basis, I should probably allow for a non-interactive version of the script.
- I’d better include the option to use Scope tags in the report capture.
- Device attributes should only be updated if they’ve changed.
- Running the script in whatif mode
- Something about Windows 11 24H2 being released.
So how does that impact this series of posts and the updated Windows 11 Accelerator script?
Graph Authentication #
Honestly I just straight up robbed the authentication function that Andrew Taylor created. Is it really stealing if it’s community content? 😘
So to allow for the updated script to authenticate to Graph. we now need to create an Entra App registration, associated Client Secret, and give the app permissions to Microsoft Graph.
Group.ReadWrite.All, Device.ReadWrite.All, DeviceManagementManagedDevices.ReadWrite.All DeviceManagementConfiguration.ReadWrite.All, User.ReadWrite.All, and DeviceManagementRBAC.Read.All
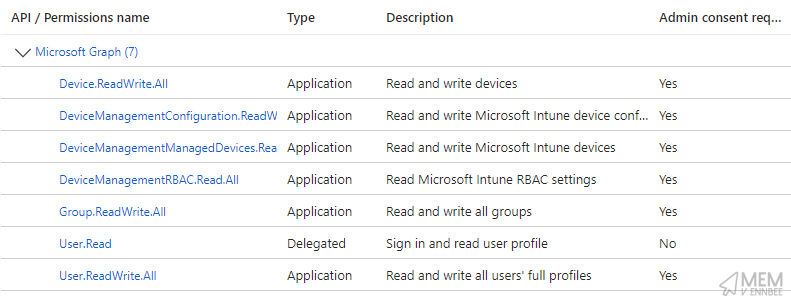
Once created, we can now pass through the Application Id and the value of the Client Secret to the script along with the already required tenant Id:
$tenantId = '36019fe7-a342-4d98-9126-1b6f94904ac7'
$appId = '297b3303-da1a-4e58-bdd2-b8d681d1bd71'
$appSecret = 'g5m8Q~CSedPeRoee4Ld9Uvg2FhR_0Hy7kUpRIbo'
.\Invoke-Windows11AcceleratorUpdate.ps1 -tenantId $tenantId -appId $appId -appSecret $appSecret -target device -featureUpdateBuild 24H2 -extensionAttribute 11
Now giving us an easier way to authenticate to Graph, and will allow you to run the script without the need to authenticate with a Global Admin account every time.
Nice.
Reporting Data Capture #
For the improvement to the script performance, well this is where thinking about enterprises with 10,000’s of Windows devices sometimes falls in a gap, when I’ve only got small dev environments to play with 😶.
Previously in the script and detailed in the below post…
…we were calling the report 50 devices at a time, and looping through Graph API calls to the deviceManagement/reports/cachedReportConfigurations endpoint to get the Feature Update Readiness report data until there were no more devices left.
Which if you’ve got 80,000 Windows devices, is going to take quite a bit of time, hours in fact.
So the solution Alberto Baratta came up with, was to just use the export report functionality that already exists in Intune, to capture the compressed download of the csv file, containing all the reporting information, using that as the source for the data.
Brilliant.
So now instead of looping through a million Graph calls, and probably hitting a throttle limit, we’re just processing the exported file.
Comparing the previous version of the script taking three minutes to run (the video has been sped up x5) for 1100 devices:
To the new version taking about three seconds:
We see a marked improvement on the time taken to gather the details of the Windows feature update compatibility risks report, meaning that even with environments with 10,000’s of devices, the process will only take seconds not minutes.
Speed nice.
Hash Tables in PowerShell #
Even with the improvement for capturing the readiness report details, when processing the data I was essentially foreach looping using Where-Object to get the deviceObjectID from the Entra data, which in large environments is not big, not clever, and importantly not quick.
So I found out about hashtables, and implemented them to vastly improve the processing of the report data.
Speedier nice.
Tagging User Objects #
I wasn’t sure about the assignment of updates to users either, but the entire device estate only contained Single User Affinity Windows devices, i.e., one device to each user, and from an awareness and communication perspective, it’s easy to tell your users when they’re going to get updates for Feature Updates than it is working out which devices are.
So a quick amendment to the script, now allows us to get details of the users from Entra, and where the primary user of the device matches one of these Entra users, it allows us to tag the user account with the risk of updating their device to Windows 11.
Running the script with a new parameter, allows us to choose whether we want to assign the risk score to user or device:
.\Invoke-Windows11AcceleratorUpdate.ps1 -target user -tenantId $tenantId -appId $appId -appSecret $appSecret -featureUpdateBuild 24H2 -extensionAttribute 11
With the script giving use the Dynamic Security Groups to create, as well as tagging primary users of the device:
Nice?
Non-Interactive Script #
So after you’ve run the script for the first time, you should be pretty happy that you’ve started tagging your devices or users, what about the subsequent runs of the script?
We should have already created our dynamic device or user groups and confirmed that the extension attributes are not in use for anything but the readiness risk state.
So I’ve now included a firstRun boolean parameter, which if set to $true (and is by default), will prompt for interaction, otherwise if set to $false will just breeze through the script and update devices with their associated update readiness risk.
.\Invoke-Windows11AcceleratorUpdate.ps1 -firstRun $false -tenantId $tenantId -target device -featureUpdateBuild 24H2 -extensionAttribute 11
Silent nice.
Intune Scope Tags #
I’d forgotten about these if I’m honest, so now I’ve included the option to select a Scope Tag, so with the change to the authentication method also included a new Graph permission of DeviceManagementRBAC.Read.All, to allow us to read the existing Scope Tags and make sure the one selected exists.
.\Invoke-Windows11AcceleratorUpdate.ps1 -scopeTag MVE -tenantId $tenantId -target device -featureUpdateBuild 24H2 -extensionAttribute 11
Don’t say I didn’t think about the more advanced users of Intune.
default is used for the Readiness report.
RBAC nice.
Attribute Updates #
I was a little lazy with the first iteration of the script, as I just leant on the fact that the call to Graph to add Device Attributes just overwrote them each time.
For more time based improvements, I’ve added in logic to only update the attributes that have changed.
Sensible nice.
Demo Mode #
Just a quick one really, and for those who are more cautious than me, you can now run the script in demo mode, where it will do everything except tag users or devices.
.\Invoke-Windows11AcceleratorUpdate.ps1 -demo -tenantId $tenantId -target device -featureUpdateBuild 24H2 -extensionAttribute 11
So this will just give you an indication of the current state of your Windows 11 Feature Update readiness, and make sure you’re not butchering your environment with tags that don’t mean anything.
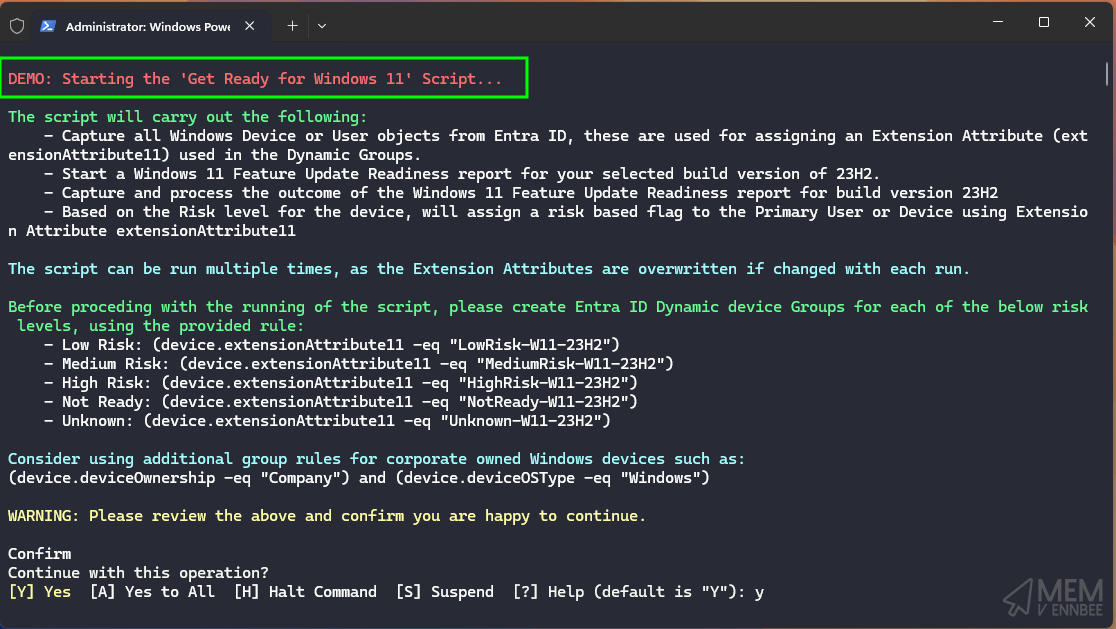
The script will still let you know what it is going to do, just not make changes to the extension attributes on devices or users.
Whatif nice.
Windows 11 24H2 #
As the Windows 11 24H2 report data is now available, we should be able to query the data in Intune. So a quick update to the calls to Graph to use GE24H2 for the correct Feature Update version (compared with NI23H2 for Windows 11 23H2), and we can get the report data and tag things with their risk state:
.\Invoke-Windows11AcceleratorUpdate.ps1 -featureUpdateBuild 24H2 -tenantId $tenantId -target device -extensionAttribute 11
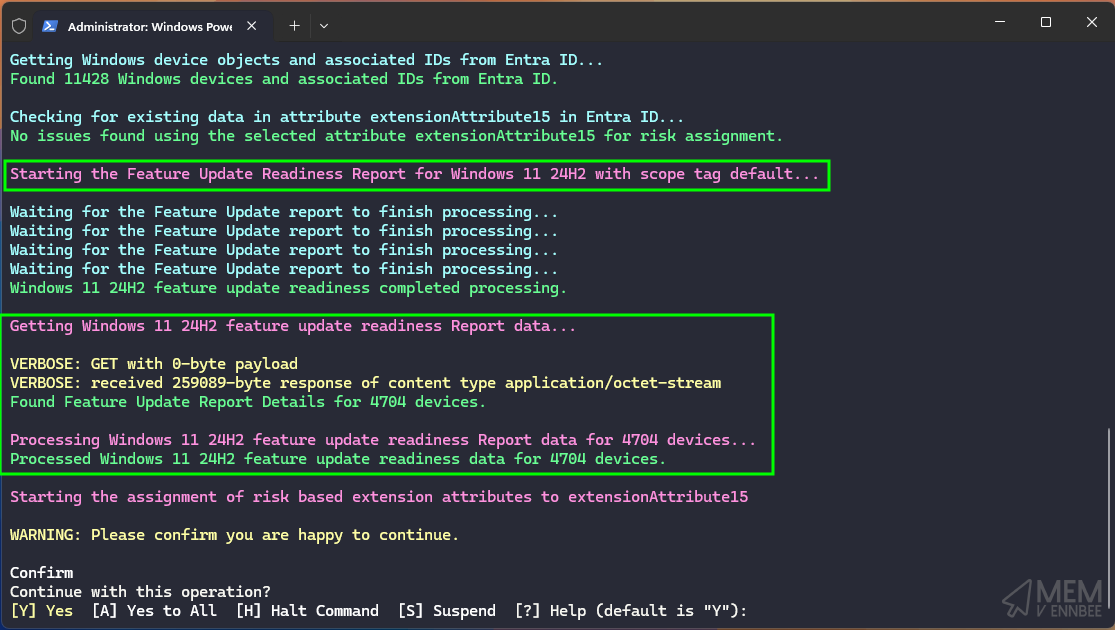
Best nice.
Summary #
Yes I know I should have probably looked at these when I first released the series of blog posts, but I didn’t. Be thankful I’ve revisited this series and not just thrown myself into Autopilot v2 or Windows 365 Link posts 😅.
Either way, you should now have no excuse to avoid moving to Windows 11 24H2 or otherwise, so crack on, start using the Windows 11 Accelerator script, time is ticking.

